Article
What is File-Level Encryption?


Read time: 3:00
Published August 4, 2025
In today’s data-driven world, security breaches and unauthorized access can result in devastating consequences—from loss of intellectual property to regulatory fines and reputational damage. One critical method of safeguarding sensitive data is file-level encryption, a technique that protects individual files rather than entire disks or databases. But what does that actually mean—and why does it matter?
File-Level Encryption Explained
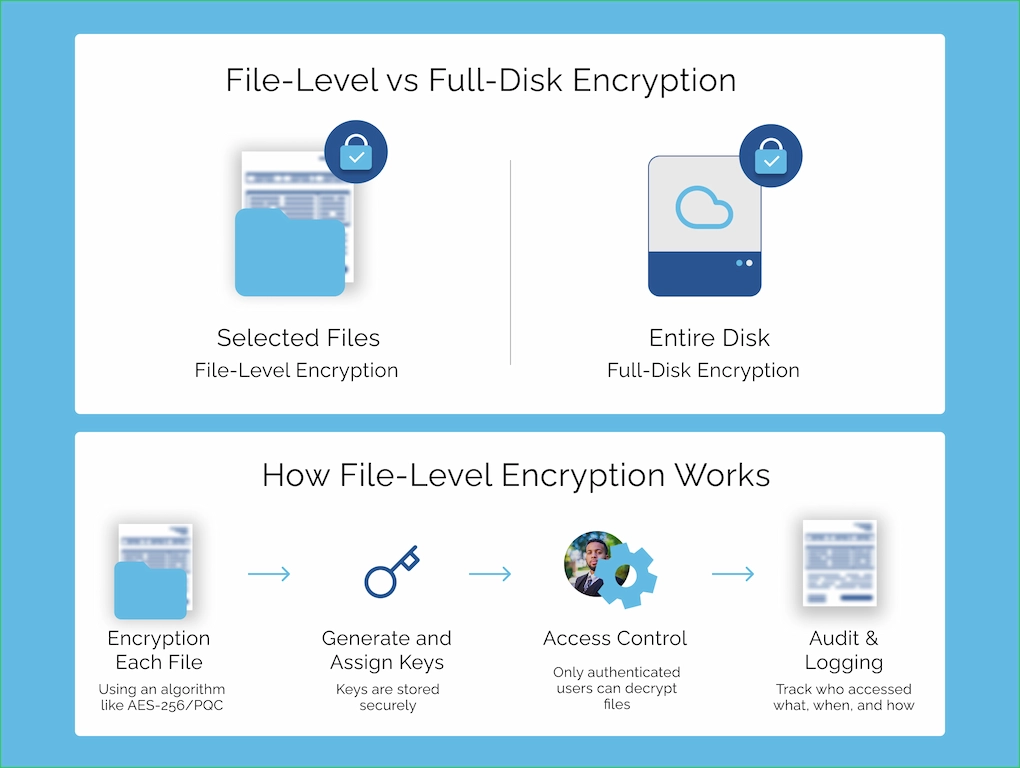
File-level encryption (FLE) is the process of encrypting individual files on a storage device or in transit so that only authorized users or systems can access the contents. Unlike full-disk encryption, which secures everything on a drive regardless of what’s being used, file-level encryption targets specific files—providing greater flexibility and precision.
Key Characteristics:
- Granular control: Only select files are encrypted, allowing for more efficient processing and selective access.
- User or role-based access: Encryption keys can be tied to user credentials or permissions, helping enforce access policies.
- Data portability: Encrypted files retain their protection even when moved, copied, or shared.
How Does File-Level Encryption Work?
- Encryption Algorithm: Each file is encrypted using an algorithm such as AES (Advanced Encryption Standard). The level of encryption (e.g., 128-bit, 256-bit) determines how difficult it is to break without the key.
- Encryption Key: To decrypt and access the file, a matching encryption key is required. These keys may be stored in secure vaults, hardware modules, or managed through enterprise key management systems.
- Access Control: Only users or applications with the right key or permissions can decrypt and read the file.
Why Use File-Level Encryption?
- Precision Security
You don’t need to encrypt an entire system—just the files that contain sensitive data like financial records, trade secrets, or medical information.
- Reduced Risk in Shared Environments
In cloud environments or shared workspaces, file-level encryption ensures that only designated recipients can access the contents, regardless of broader system access.
- Compliance and Legal Protection
Regulations like HIPAA, GDPR, and CJIS require organizations to protect personal and sensitive data. File-level encryption is often a key part of demonstrating compliance.
- Survivability After Breach
Even if attackers breach the system perimeter, encrypted files remain unintelligible without the appropriate decryption keys.
File-Level vs. Full-Disk vs. Database Encryption
| Encryption Type | Scope | Best For |
| File-Level | Individual files | Precision access control, cloud or shared storage |
| Full-Disk | Entire drive | Laptop security, lost device protection |
| Database | Specific data fields or tables | Large-scale systems, structured data at rest |
In practice, many organizations use a combination of these approaches to layer their defenses.
Challenges of File-Level Encryption
- Key management complexity: Lost keys mean lost data.
- Performance overhead: Encryption can add processing time, although this is minimal with modern algorithms.
- Implementation inconsistency: Not all systems or applications support FLE natively, requiring additional tooling.
Final Thoughts
As cyber threats grow in sophistication, protecting data at the most granular level becomes not just a best practice—but a necessity. File-level encryption offers a powerful and flexible way to protect high-value files wherever they reside. Whether you’re managing personal documents, enterprise secrets, or regulated data, adopting FLE can be a smart and scalable step toward better security.
What This Means for Security Teams
- Begin inventorying cryptographic assets now. Download Free Cybersecurity Checklist.
- Follow NCSC guidance to prepare for PQC.
- Locktera offers automated tools to help you identify and upgrade vulnerable systems. Start a Free Trial.
