Locktera: Cybersecurity Checklist
Download: Cybersecurity Checklist for File-Level Protection
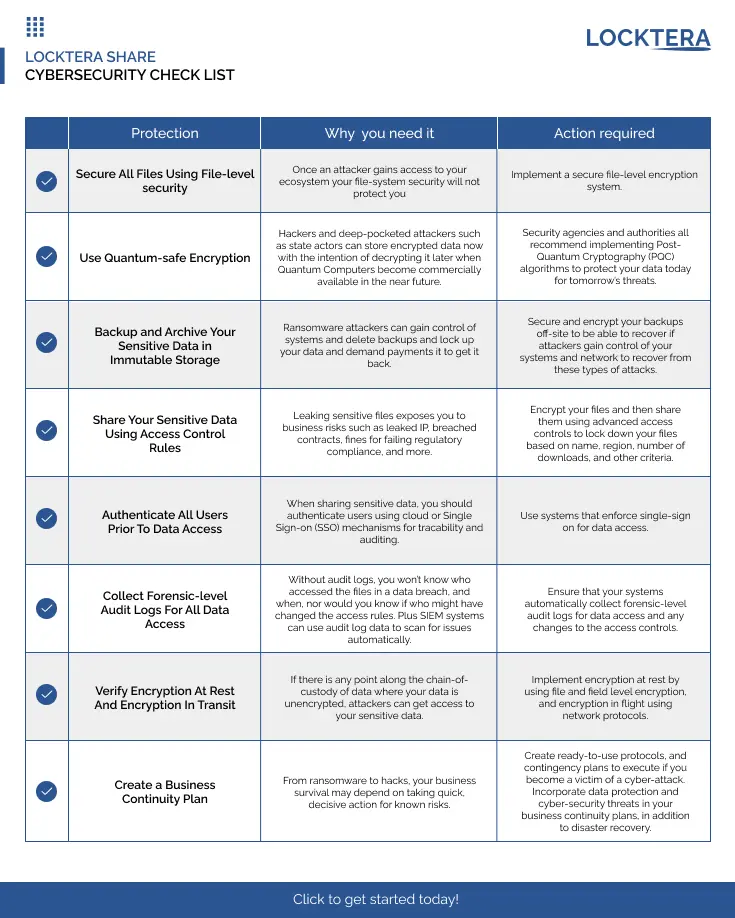
Cyber threats are evolving fast—and so should your defense. This Cybersecurity Checklist gives you a clear, actionable roadmap for protecting your organization’s most sensitive data from modern threats like ransomware, insider risk, and quantum-era decryption.
Built around best practices recommended by top security authorities, this checklist walks you through the essentials—from file-level encryption and access controls, to immutable backups, forensic audit trails, and business continuity planning.
Download now to assess your current posture and implement the protections that matter most—before an attacker forces the issue.
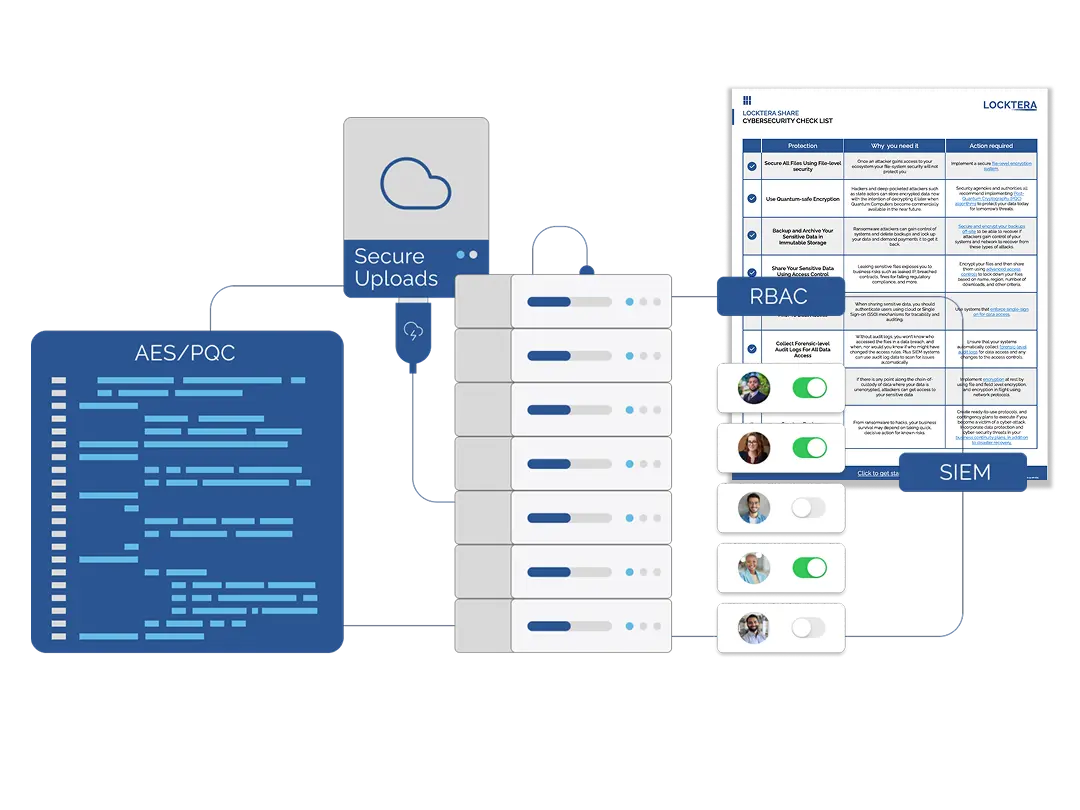
File-Level Encryption with Off-Site Backup
Locktera enables off-site backups secured with file-level encryption — ensuring your files remain untampered and retrievable, even if your local systems are compromised.
- Secure each file individually with AES + PQC encryption
- Replicate encrypted files across regions or cloud providers
- Restore quickly with full data integrity
Make Locktera Part of Your Business Continuity & Disaster Recovery Plan
Protect what matters most — your data.
In the face of disruption, Locktera ensures your files remain secure, accessible, and under your control.
File-Level Protection that Withstands Outages
Locktera’s file-level encryption and granular access controls keep your most sensitive content protected even during unforeseen events. Whether it’s a system failure, ransomware attack, or a natural disaster, your data remains intact and retrievable.
Rapid Recovery with Zero Downtime
With Locktera, your critical data can be stored on any cloud or hybrid infrastructure — including Azure, AWS, Google Cloud, Wasabi, and more. In the event of a failure, switch instantly to secondary storage endpoints using our built-in portability.
- Distribute data across regions
- Instant failover with redundant storage targets
- No vendor lock-in
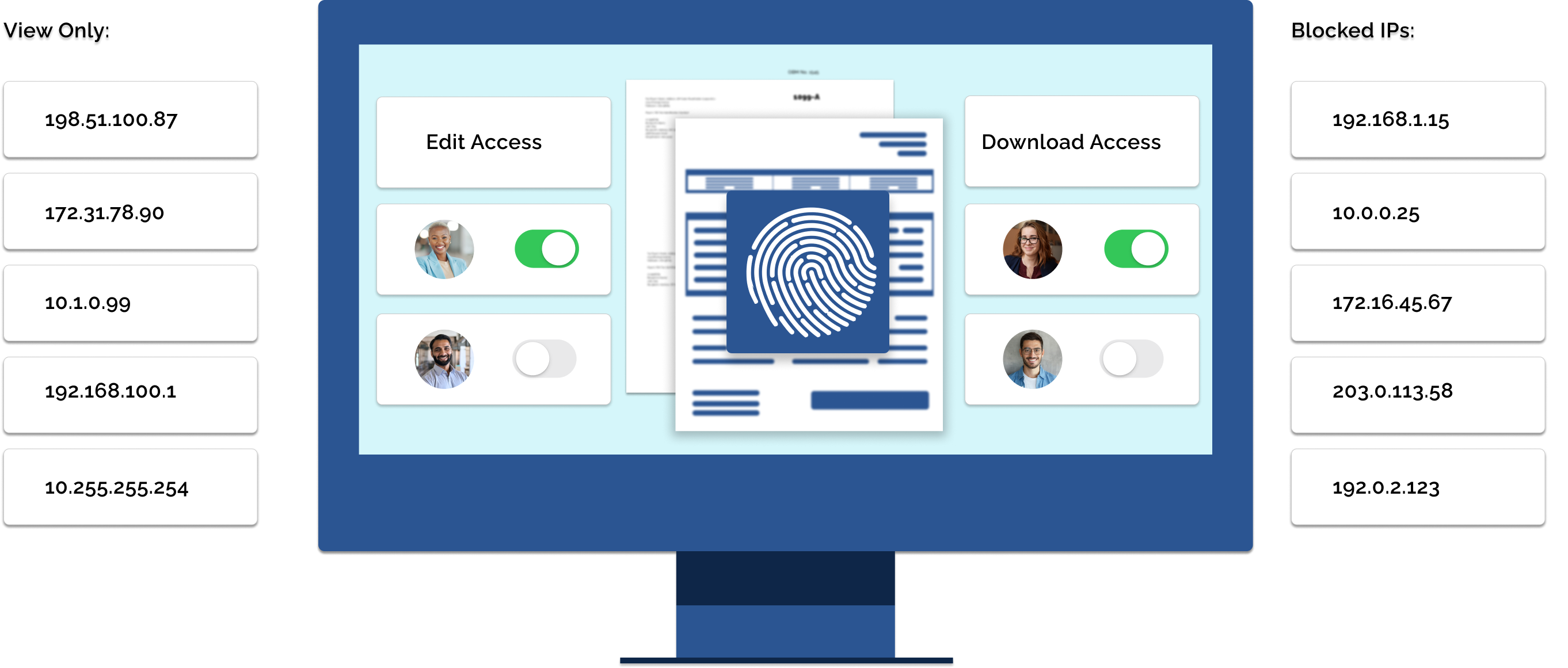
Customizable Access Controls for Secure Document Sharing
Locktera Share provides powerful access control features, enabling you to customize permissions for each document shared. You can set specific access levels such as read only, or download permission, ensuring that only authorized users can interact with your files. Additionally, you can apply advanced restrictions based on user roles, IP addresses, or even geographic locations, giving you fine-tuned control over who can access your sensitive information.
Real-Time Engagement Analytics for Complete Document Visibility and Control
The platform also offers detailed engagement analytics, giving you real-time visibility into how your documents are being used. You can track who has viewed, downloaded, or shared files, and monitor user activity to ensure compliance with internal policies and regulations. These insights allow you to maintain control over your documents and detect any potential security risks or unauthorized access.