Fortify Your Business Continuity Strategy with Locktera
Locktera keeps your mission-critical files secure and accessible — even during outages, cyberattacks, or operational disruptions. By combining file-level encryption, enforced access controls, and immutable audit logging, Locktera enables your team to share, back up, and recover sensitive data with confidence, while maintaining full compliance and control at every step.
File-Level Protection that Withstands Outages
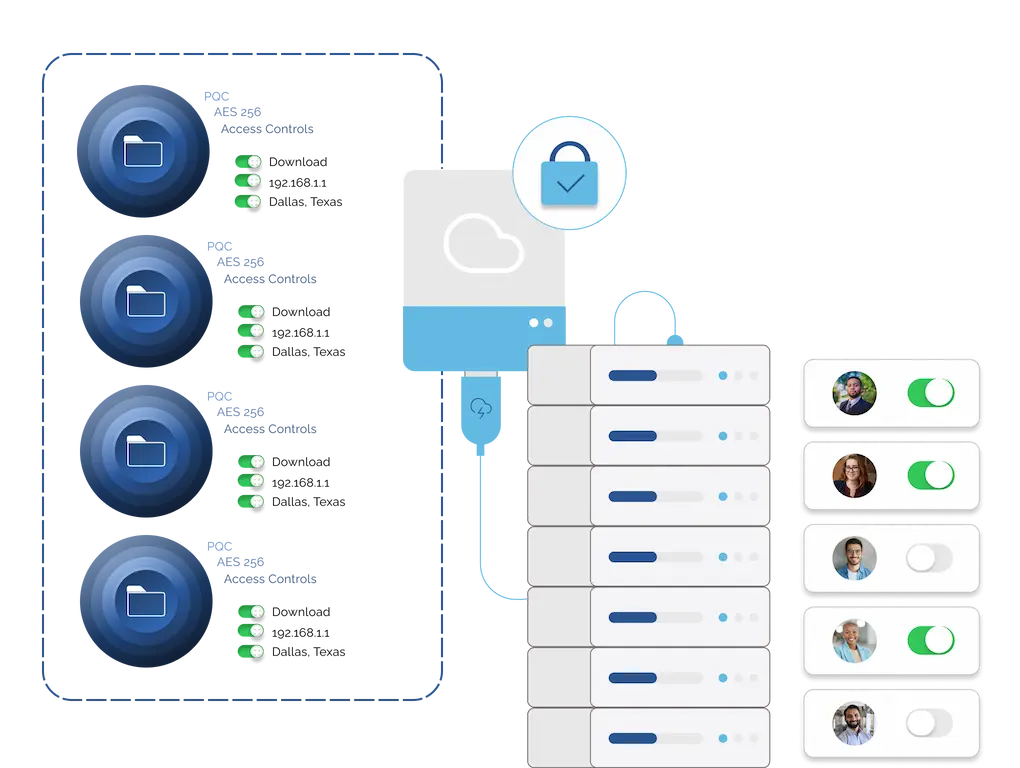
Locktera’s file-level encryption and granular access controls keep your most sensitive content protected even during unforeseen events. Whether it’s a system failure, ransomware attack, or a natural disaster, your data remains intact and retrievable.
Have Questions About Locktera Security?
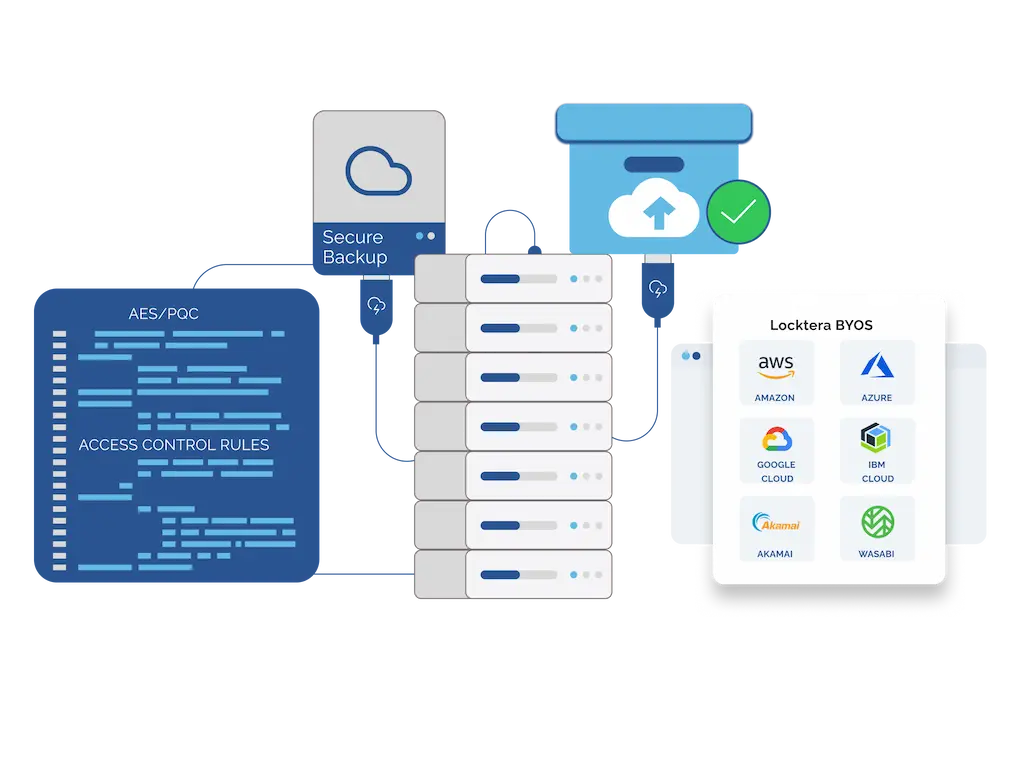
Backup and Recovery, Without the Risk
Decentralized Backup
Store encrypted .tera files in any location — on-prem, cloud, or hybrid — without losing control of permissions.
Policy-Driven Expiry and Revocation
Disable access instantly in the event of a breach or role change.
No Downtime Dependence
Files remain protected and policy-bound even when offline or shared externally.
Zero-Knowledge Architecture
Only your organization has access to file contents — Locktera never holds your keys.
Have a Question? We’re Here to Help.
Integrate Locktera Into Your Continuity Stack
Locktera’s developer APIs enable seamless integration with your existing infrastructure — including incident response platforms, secure content management systems, evidence archiving workflows, and cloud or hybrid storage environments. Every integration maintains Locktera’s core security standards, including file-level encryption, granular access controls, and immutable audit logging, while supporting compliance with frameworks like HIPAA, CJIS, GDPR, and SOC 2.
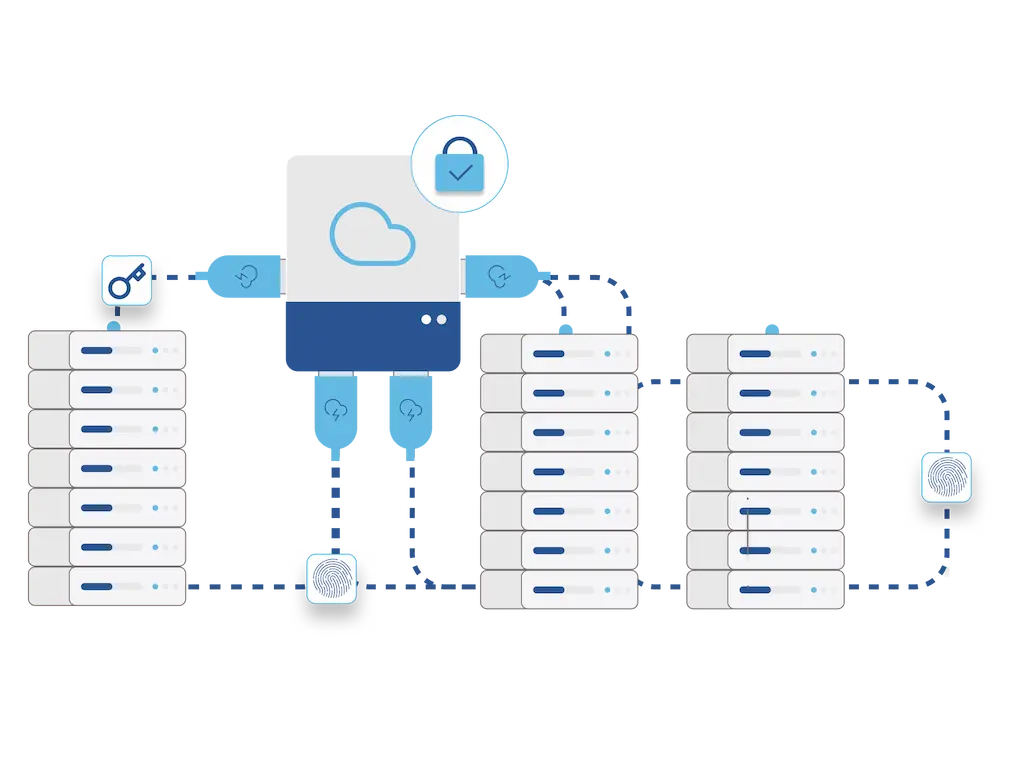
Rapid Recovery with Zero Downtime
With Locktera, your critical data can be stored on any cloud or hybrid infrastructure — including Azure, AWS, Google Cloud, Wasabi, and more. In the event of a failure, switch instantly to secondary storage endpoints using our built-in portability.
- Distribute data across regions
- Instant failover with redundant storage targets
- No vendor lock-in
Make Locktera Part of Your Business Continuity & Disaster Recovery Plan
Protect what matters most — your data.
In the face of disruption, Locktera ensures your files remain secure, accessible, and under your control.
Resilient by Design
Revoke Access in Real Time
In case of a breach or active threat, Locktera allows administrators to instantly revoke file access across all users, groups, or applications.
- Trigger a global kill switch to block access
- Automatically expire access rules
- Contain threats before they spread
Ransomware-Resistant Architecture
Locktera containers are write-once-read-many (WORM) compliant and can be configured to lock files for a specific duration, preventing unauthorized changes or deletions — even from internal actors.
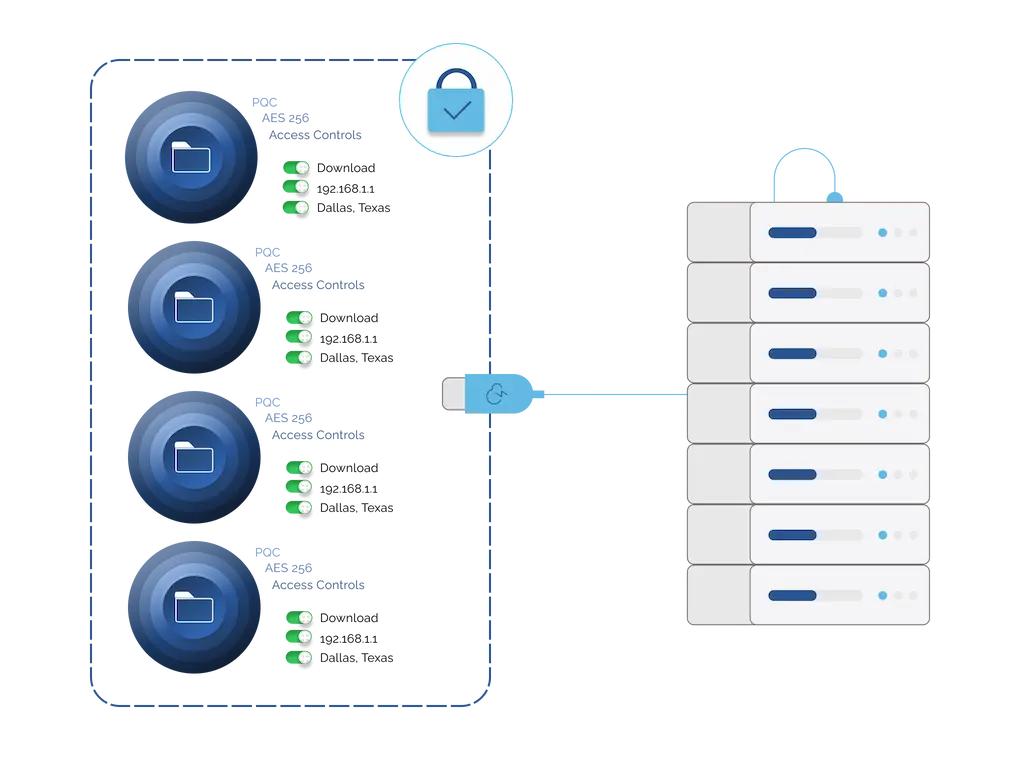
Audit Reports to Assess Damage
Know exactly what was accessed — and when.
Locktera maintains real-time audit trails and access logs so your team can quickly assess the scope of impact during an incident.
- View complete history of file access, sharing, and downloads
- Filter by user, file, or time period
- Export logs for compliance or investigation
