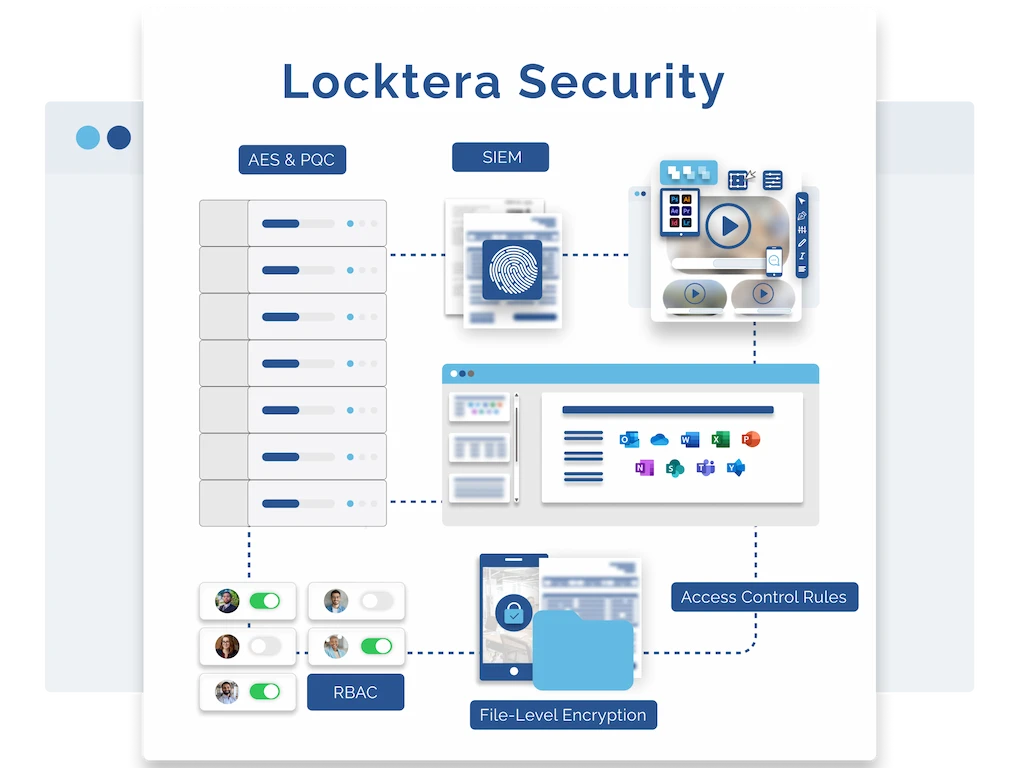
End-to-End, Client-Side Encryption for Maximum Security
Locktera uses true end-to-end encryption with client-side key generation, ensuring that only the sender and authorized recipients can access the contents of a file. Files are encrypted before they ever leave your device—and can’t be decrypted by Locktera or any intermediary. This means your data stays protected at every stage: in transit and at rest. Whether you’re sharing sensitive documents or proprietary information, Locktera’s encryption model guarantees privacy, integrity, and control in a zero-trust world.
Have Questions About Locktera End-To-End Encryption?
Have a Question? We’re Here to Help.
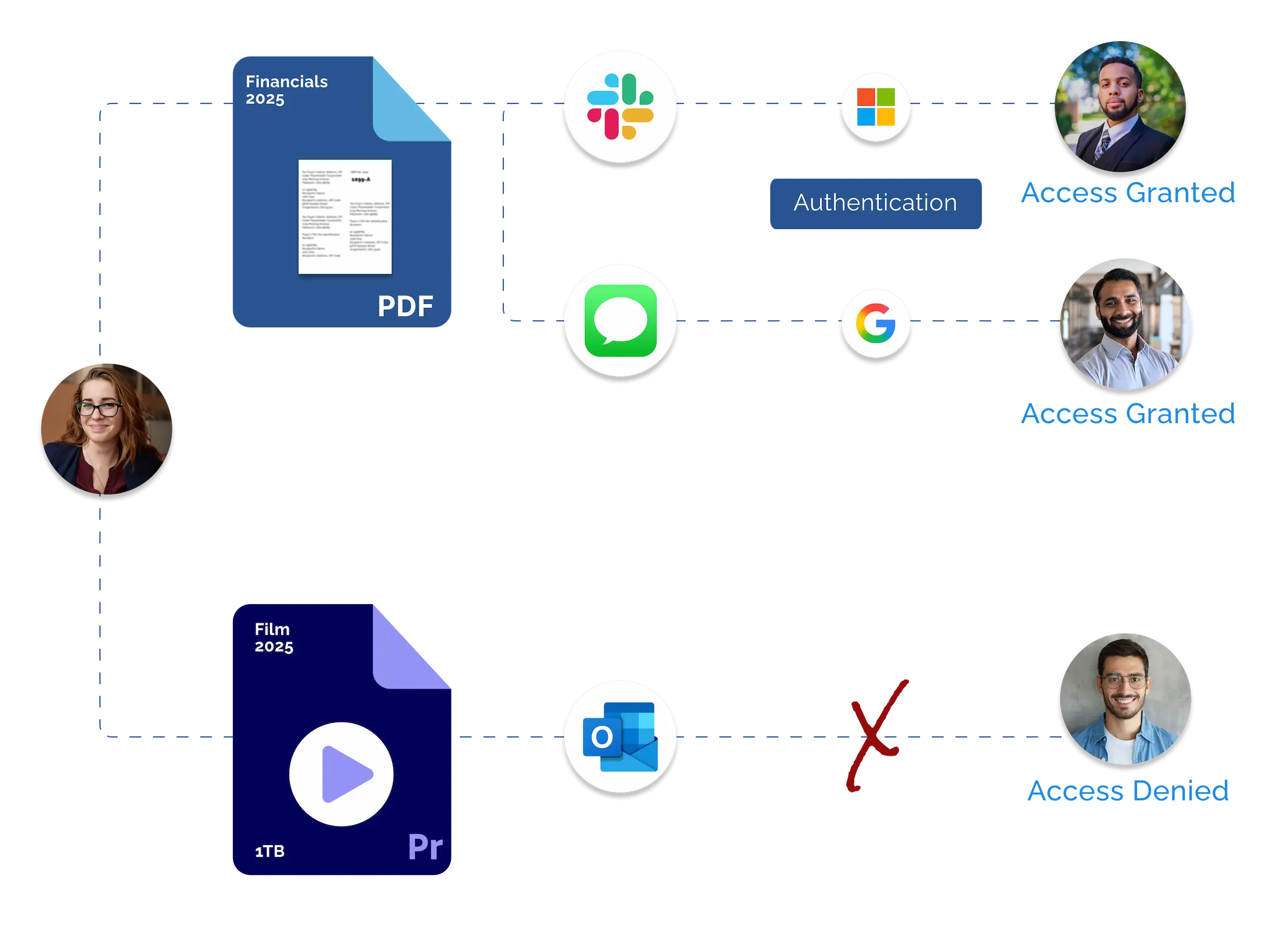
Secure Access, Defined by You
With Locktera, you can upload multiple files into a single secure container, then apply precise, granular permissions before sharing. Define exactly who can access the content—based on user roles, groups, timeframes, or other conditions—and Locktera enforces those rules before any file can be opened. Once permissions are set, the container is encrypted and ready to share, giving you full control over how, when, and by whom your sensitive data is accessed.
Password Lockout Protection That Puts You in Control
Locktera lets users configure the number of allowed password attempts before a viewer is locked out of a secure container. If someone exceeds the set limit without success, access is automatically blocked—protecting your content from brute-force attacks or unauthorized entry. Only the original user can manually unlock the container, giving you full control over when and if a viewer can try again. It’s a simple, powerful safeguard that keeps your shared data secure.
Revoke Access Instantly—From Anywhere
Locktera gives you the power to revoke access to any secure container at any time, from any location. Whether due to a policy change, employee departure, or potential security risk, you can immediately disable access with a single action—no need to chase down copies or rely on third parties. Once revoked, all permissions are blocked, and the encrypted container becomes inaccessible to anyone, ensuring your data stays protected even after it’s been shared.
Have Questions About Locktera Security?
Enforce Browser Time-Outs to Limit Risk and Lock Down Sessions
Locktera lets system administrators define strict browser time-out rules to reduce exposure from idle sessions. Assign separate inactivity limits for internal users and external viewers—ensuring shared content is never left open or unattended. If no activity is detected within the designated window, Locktera automatically logs out the session and secures access. Whether accessed by your team or third-party recipients, every interaction is time-bound and tightly controlled.
