Build security directly into your workflows with Locktera CORE
The developer API platform that brings advanced encryption, access control, and audit logging to your applications.
Whether you’re building a document sharing portal, a digital evidence system, or a secure enterprise archive, Locktera CORE gives you the tools to protect files at the container level — even after they’ve been shared or downloaded.
Locktera API in Action
File Level Security
Each individual document is protected at its core, safeguarding sensitive data even if the system is compromised.
Quantum Safe Encryption
Protect data from future threats posed by quantum computing, ensuring that sensitive information remains secure even as technology advances.
Access Control Rules
Reduce the risk of unauthorized access and maintain compliance with industry regulations by enforcing strict control over information within your organization.
SafeSend Request
AI Security
Safeguard AI data sets, preventing unauthorized access and maintaining the integrity of your data assets.
IoT Security
Protect data transmitted by connected devices ensuring that sensitive information is encrypted and safeguarded.
Upload documents or form data to secure container
Ensure all sensitive data is encrypted and stored in a protected container, preventing unauthorized access or tampering.
Secure archive files
Locktera’s security framework prevents unauthorized access and ensures that archived information remains compliant with industry regulations, safeguarding your data for future retrieval.
Software Updates
Ensure the security and integrity of software updates by employing cutting-edge encryption protocols
Powerful Tools You Can Unlock with Locktera CORE
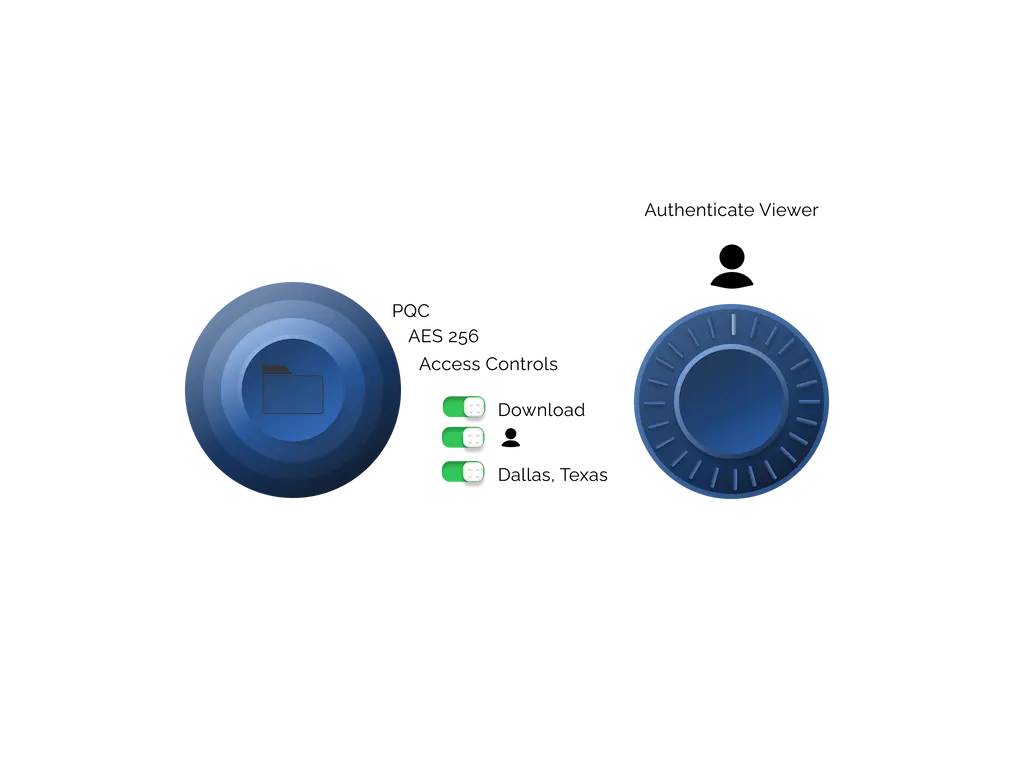
- Encrypt and containerize files with PQC and AES-256 in Locktera’s proprietary .tera format to maintain protection across systems and users
- Enforce persistent file-level security that travels with the file—regardless of where or how it’s shared
- Authenticate access using SSO, TOTP-based MFA, or federated identity providers like Entra ID and Okta
- Define granular access policies such as view-only mode, expiration dates, download blocking, and domain restrictions
- Preserve file immutability by locking content at the time of encryption—ensuring that no one, including administrators, can alter the file after it’s sealed
- Track every event with immutable audit logs capturing opens, downloads, access attempts, and permission changes
- Securely back up and archive sensitive files while maintaining full control over access, compliance, and retention policies
- Integrate seamlessly via REST API with cloud storage, internal systems, or evidence workflows to automate secure content handling

Experience the power of Locktera firsthand.
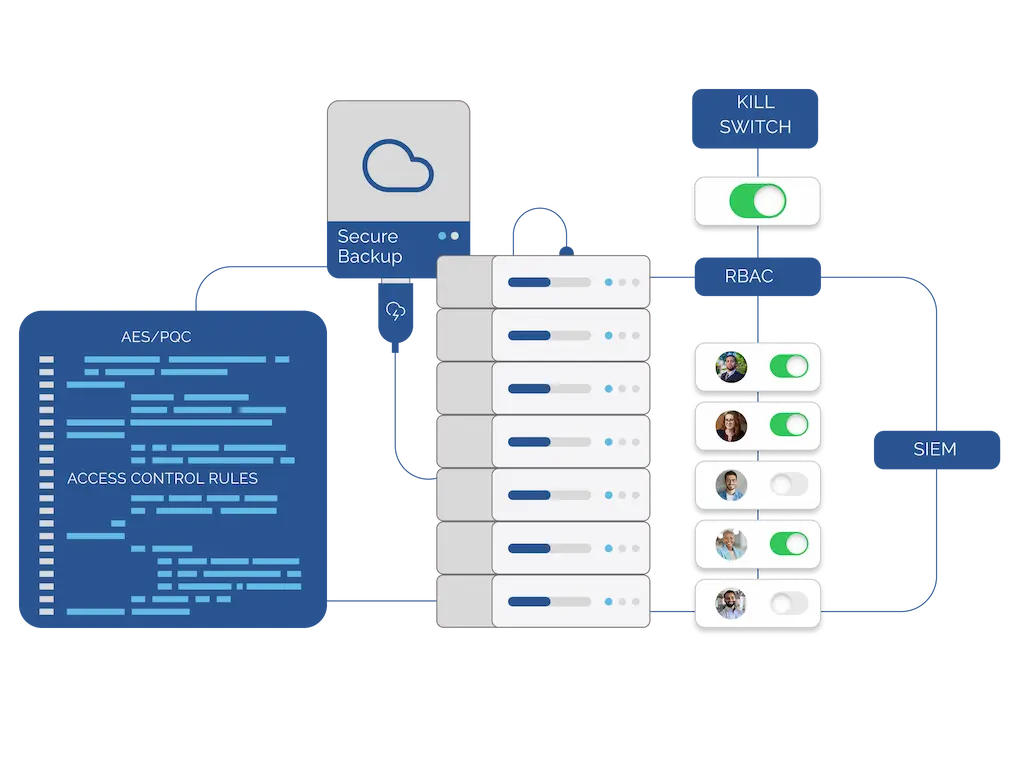
Instantly Deploy Quantum Resistant Security With Locktera CORE™
As the digital landscape evolves, protecting critical data from cyberattacks has become paramount. Locktera’s Security APIs provide advanced security features, enabling businesses to strengthen their defenses and comply with stringent regulatory standards.
Experience the power of Locktera firsthand.

Prevent injection of malicious code
Reduce attack surface with file level security