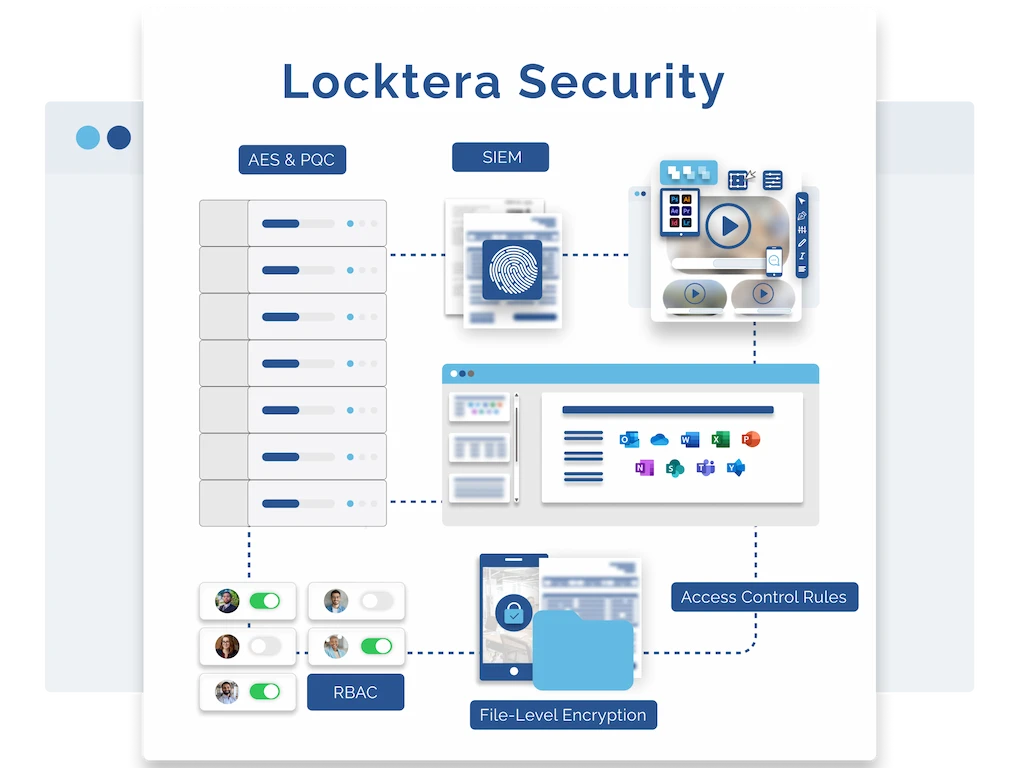
Secure Everything. Sacrifice Nothing.
Locktera’s security framework is built from the ground up to protect sensitive data across every stage of its lifecycle. Our approach goes far beyond basic encryption—combining file-level protection, post-quantum cryptography, granular access controls, and deep audit capabilities to create a zero-compromise environment for secure file sharing and storage. Whether you’re safeguarding proprietary files or meeting strict regulatory standards, Locktera delivers the transparency, control, and resilience modern organizations demand. Learn more about Locktera’s robust security features:
Granular Protection, File by File
Benefits of File-Level Encryption
| Benefits | Description |
|---|---|
| Granular Protection | Each file is independently encrypted using advanced methods such as AES-256 and post-quantum cryptography (PQC), ensuring that even if part of the system is compromised, individual files remain protected. This file-level encryption isolates sensitive data, so a breach in one system, folder, or user account does not expose other files—providing true compartmentalized security. |
| Reduced Attack Surface | Locktera significantly reduces the attack surface available to hackers. Even if an attacker gains access to a device or system, each file remains individually encrypted—requiring separate decryption efforts. This layered security approach makes it far more difficult to extract usable data, effectively minimizing the risk of large-scale breaches. |
| Data Mobility and Flexibility | Locktera’s file-level encryption ensures that files remain secure wherever they go, whether stored on local drives, shared across networks, or uploaded to the cloud. It supports secure file sharing between users or third parties, ensuring that data remains protected during transmission and access is restricted to authorized users. |
| Simplified Breach Response | In the event of a security breach, Locktera’s file-level encryption ensures that sensitive files remain secure, even if unauthorized access to the broader system occurs. This containment reduces the need for extensive remediation and breach notifications, as encrypted files are less likely to result in the disclosure of sensitive information. |
| Compatibility with Multiple Environments | Locktera’s file-level encryption is compatible with various environments, including cloud storage, on-premises systems, and hybrid infrastructures. Whether files are stored locally or remotely, Locktera maintains the same high level of security, ensuring consistent data protection across platforms. |
| Digital Rights Management (DRM) | Locktera incorporates DRM policies at the file level, which allows organizations to control how files are used even after they’ve been shared. DRM ensures that files cannot be copied, edited, or printed without proper authorization. This gives organizations the power to restrict usage of sensitive files beyond just access control, preventing data misuse or leaks. |
| Audit Trails and Monitoring | Locktera provides detailed audit logs for each file, showing who accessed it, when, and what actions were taken (view, edit, share, etc.). These logs are essential for monitoring file usage and detecting any unauthorized or suspicious activity, enhancing security oversight. |
| User Accountability | File-level security promotes user accountability by tracking actions on a per-file basis. This visibility ensures that users are held responsible for their interactions with sensitive data. It deters malicious insiders or unauthorized actions by ensuring that every access or modification is recorded. |
Granular Protection
Each file is independently encrypted using advanced methods such as AES-256 and post-quantum cryptography (PQC), ensuring that even if part of the system is compromised, individual files remain protected. This file-level encryption isolates sensitive data, so a breach in one system, folder, or user account does not expose other files—providing true compartmentalized security.
Reduced Attack Surface
Locktera significantly reduces the attack surface available to hackers. Even if an attacker gains access to a device or system, each file remains individually encrypted—requiring separate decryption efforts. This layered security approach makes it far more difficult to extract usable data, effectively minimizing the risk of large-scale breaches.
Data Mobility and Flexibility
Locktera’s file-level encryption ensures that files remain secure wherever they go, whether stored on local drives, shared across networks, or uploaded to the cloud. It supports secure file sharing between users or third parties, ensuring that data remains protected during transmission and access is restricted to authorized users.
Simplified Breach Response
In the event of a security breach, Locktera’s file-level encryption ensures that sensitive files remain secure, even if unauthorized access to the broader system occurs. This containment reduces the need for extensive remediation and breach notifications, as encrypted files are less likely to result in the disclosure of sensitive information.
Compatibility with Multiple Environments
Locktera’s file-level encryption is compatible with various environments, including cloud storage, on-premises systems, and hybrid infrastructures. Whether files are stored locally or remotely, Locktera maintains the same high level of security, ensuring consistent data protection across platforms.
Digital Rights Management (DRM)
Locktera incorporates DRM policies at the file level, which allows organizations to control how files are used even after they’ve been shared. DRM ensures that files cannot be copied, edited, or printed without proper authorization. This gives organizations the power to restrict usage of sensitive files beyond just access control, preventing data misuse or leaks.
Audit Trails and Monitoring
Locktera provides detailed audit logs for each file, showing who accessed it, when, and what actions were taken (view, edit, share, etc.). These logs are essential for monitoring file usage and detecting any unauthorized or suspicious activity, enhancing security oversight.
User Accountability
File-level security promotes user accountability by tracking actions on a per-file basis. This visibility ensures that users are held responsible for their interactions with sensitive data. It deters malicious insiders or unauthorized actions by ensuring that every access or modification is recorded.
File-Level Over Standard Disc Encryption
File-level encryption is essential for protecting sensitive data. Unlike system- or disk-level encryption, it secures each file individually, giving you precise control over what’s protected, who can access it, and how it’s managed. Even if a system is breached, encrypted files remain unreadable without the proper keys.
In today’s environment—where data moves across networks, cloud platforms, and third-party tools—this granular protection is more important than ever. File-level encryption also supports compliance with regulations like GDPR and HIPAA, helping organizations safeguard critical information and reduce the risk of large-scale breaches.
Have Questions About Locktera Security?
File-Level Versus Standard Disc Encryption
| Feature | Locktera File Level Encryption | Standard Disk or Storage Encryption |
|---|---|---|
| Granularity of Security | Locktera secures individual files rather than the entire disk. This means you can apply encryption to specific files or folders, giving you more control over what is protected. Different files can have different encryption keys and access controls, allowing selective encryption based on the sensitivity of the data. | Encrypts an entire disk or storage device. Once the system or device is unlocked (such as by logging in), all data is accessible to authorized users without further control at the file level. |
| Selective Access Control | With Locktera’s file-level encryption, access can be granted to specific users or groups based on need—ensuring each file is only available to those who require it. This is ideal for managing varying confidentiality levels and stakeholder access. | Provides access to all data once unlocked, making it less flexible in environments where selective access is crucial. |
| Protection in Motion | Locktera protects files even when they are in transit or shared outside of their original storage environment. This ensures that files remain encrypted regardless of where they are stored or how they are transferred (e.g., via email, cloud services). | Secures the data only when it is on the device. If the data is moved to another system or shared, it may lose its encryption unless additional measures are taken. |
| Revocation and Expiry | Locktera supports revoking access or setting expiry dates for files. This means that even after a file has been shared, access to it can be removed remotely, providing ongoing control. | Doesn't offer this level of control. Once access to the system or device is granted, there is no further ability to revoke access to specific data. |
| Auditability and Monitoring | Locktera provides detailed audit logs, allowing you to track who accessed or attempted to access specific files, when, and from where. This is crucial in industries that require compliance with security standards (e.g., finance, healthcare). | Typically lacks this feature since it is concerned with securing data at the device or storage level rather than managing and auditing individual file accesses. |
| Protection Against Insider Threats | Locktera protects files even from users who have access to the underlying system or disk. For example, administrators might have access to the disk but not the files encrypted at the file level, providing another layer of protection. | Doesn't provide this level of protection, as anyone with access to the disk after it's unlocked can potentially access all files. |
Granularity of Security
File-Level Encryption:
Locktera secures individual files rather than the entire disk. This means you can apply encryption to specific files or folders, giving you more control over what is protected. Different files can have different encryption keys and access controls, allowing selective encryption based on the sensitivity of the data.
System Disc Encryption:
Encrypts an entire disk or storage device. Once the system or device is unlocked (such as by logging in), all data is accessible to authorized users without further control at the file level.
Selective Access Control
File-Level Encryption:
With Locktera’s file-level encryption, access can be granted to specific users or groups based on need—ensuring each file is only available to those who require it. This is ideal for managing varying confidentiality levels and stakeholder access.
System Disc Encryption:
Provides access to all data once unlocked, making it less flexible in environments where selective access is crucial.
Protection In Motion
File-Level Encryption:
Locktera protects files even when they are in transit or shared outside of their original storage environment. This ensures that files remain encrypted regardless of where they are stored or how they are transferred (e.g., via email, cloud services).
System Disc Encryption:
Secures the data only when it is on the device. If the data is moved to another system or shared, it may lose its encryption unless additional measures are taken.
Revocation And Expiry
File-Level Encryption:
Locktera supports revoking access or setting expiry dates for files. This means that even after a file has been shared, access to it can be removed remotely, providing ongoing control.
System Disc Encryption:
Doesn’t offer this level of control. Once access to the system or device is granted, there is no further ability to revoke access to specific data.
Audibility and Monitoring
File-Level Encryption:
Locktera provides detailed audit logs, allowing you to track who accessed or attempted to access specific files, when, and from where. This is crucial in industries that require compliance with security standards (e.g., finance, healthcare).
System Disc Encryption:
Typically lacks this feature since it is concerned with securing data at the device or storage level rather than managing and auditing individual file accesses.
Protection Against Insider Threats
File-Level Encryption:
Locktera protects files even from users who have access to the underlying system or disk. For example, administrators might have access to the disk but not the files encrypted at the file level, providing another layer of protection.
System Disc Encryption:
Doesn’t provide this level of protection, as anyone with access to the disk after it’s unlocked can potentially access all files.
Locktera Delivers Hybrid AES-256 and PQC Encryption
Locktera combines the proven strength of AES-256 with cutting-edge post-quantum cryptography (PQC) to secure your files against today’s threats and tomorrow’s quantum risks. This hybrid approach ensures long-term data protection, making your encryption future-ready without compromising performance.
AES-256 Encryption Benefits
| Benefits of AES-256 | Description |
|---|---|
| High Level Security | One of the highest levels of encryption security available today. With its 256-bit key length, it offers a practically unbreakable level of security against brute-force attacks. It would take an astronomical amount of time and computing power for an attacker to successfully guess a 256-bit key. |
| Quantum-Resistant (for now) | AES-256 remains one of the strongest symmetric encryption standards available, but it's not immune to quantum threats. Quantum algorithms like Grover’s can effectively cut its security level in half—reducing AES-256 to the equivalent of 128-bit security. While this still offers robust protection, it highlights the limitations of symmetric encryption in a quantum computing world. As quantum machines continue to advance, even AES-256 may eventually be challenged, underscoring the growing importance of post-quantum cryptographic solutions. |
| Widely Adopted and Trusted | Widely implemented across industries and has been standardized by NIST (National Institute of Standards and Technology) as a secure encryption algorithm. It is used by governments, military, and financial institutions globally, providing a level of trust and reliability in the algorithm. |
| Efficient Performance | Despite its strong security, AES-256 is also relatively efficient in terms of computational power and speed, especially when implemented in hardware. Many processors have built-in hardware acceleration for AES, further improving performance. |
| Versatile and Flexible | Used for encrypting a wide range of data types and is suitable for a variety of applications, including file encryption, communications security (TLS), disk encryption (BitLocker, FileVault), and VPNs. |
| Compliance and Regulatory Acceptance | Recognized by many data protection regulations, including GDPR, HIPAA, and PCI DSS, as a best practice for securing sensitive data. This ensures compliance with legal standards for encryption in various industries. |
| Symmetric Key Encryption | AES-256 is a symmetric encryption algorithm, meaning the same key is used for both encryption and decryption. This makes key management simpler in many cases, as only one key needs to be securely stored and transmitted between parties. |
| Resistance to Known Attacks | Extensively studied and resistant to all known practical cryptographic attacks, such as differential, linear, and side-channel attacks. Its design has stood the test of time, with no serious vulnerabilities discovered since its adoption. |
High Level Security
One of the highest levels of encryption security available today. With its 256-bit key length, it offers a practically unbreakable level of security against brute-force attacks. It would take an astronomical amount of time and computing power for an attacker to successfully guess a 256-bit key.
Quantum Resistant For Now
AES-256 remains one of the strongest symmetric encryption standards available, but it’s not immune to quantum threats. Quantum algorithms like Grover’s can effectively cut its security level in half—reducing AES-256 to the equivalent of 128-bit security. While this still offers robust protection, it highlights the limitations of symmetric encryption in a quantum computing world. As quantum machines continue to advance, even AES-256 may eventually be challenged, underscoring the growing importance of post-quantum cryptographic solutions.
Widely Adopted and Trusted
Widely implemented across industries and has been standardized by NIST (National Institute of Standards and Technology) as a secure encryption algorithm. It is used by governments, military, and financial institutions globally, providing a level of trust and reliability in the algorithm.
Efficient Performance
Despite its strong security, AES-256 is also relatively efficient in terms of computational power and speed, especially when implemented in hardware. Many processors have built-in hardware acceleration for AES, further improving performance.
Versatile and Flexible
Used for encrypting a wide range of data types and is suitable for a variety of applications, including file encryption, communications security (TLS), disk encryption (BitLocker, FileVault), and VPNs.
Compliance and Regulatory Acceptance
Recognized by many data protection regulations, including GDPR, HIPAA, and PCI DSS, as a best practice for securing sensitive data. This ensures compliance with legal standards for encryption in various industries.
Symmetric Key Encryption
AES-256 is a symmetric encryption algorithm, meaning the same key is used for both encryption and decryption. This makes key management simpler in many cases, as only one key needs to be securely stored and transmitted between parties.
Resistance To Known Attacks
Extensively studied and resistant to all known practical cryptographic attacks, such as differential, linear, and side-channel attacks. Its design has stood the test of time, with no serious vulnerabilities discovered since its adoption.
PQC Encryption Benefits
Locktera uses the post-quantum cryptographic algorithm Falcon to protect data against both classical and emerging quantum threats, ensuring long-term security as quantum computing continues to evolve.
| Benefits Of PQC | Description |
|---|---|
| Low Overhead Cost | Falcon offers fast and lightweight signature verification, making it ideal for applications that need to process a high volume of transactions or messages quickly. |
| Compact Signature Size | Falcon has one of the smallest signature sizes among post-quantum algorithms, which is highly advantageous for applications where bandwidth, storage, or transmission size is limited (e.g., embedded systems, IoT devices). |
| Efficient Key Generation and Signing | Falcon provides efficient key generation and signing processes, making it more suitable for environments with limited computational resources. |
| Lattice-based Security | Falcon is based on lattice-based cryptography, which is widely regarded as one of the most secure cryptographic foundations in the post-quantum era. It provides strong security guarantees against both classical and quantum attacks. |
| NIST Standardization | Falcon has been selected as one of the finalists in the National Institute of Standards and Technology (NIST) post-quantum cryptography standardization process, lending it credibility and trust for future applications. |
| Post-Quantum Security | Falcon is resistant to quantum attacks, particularly Shor’s algorithm, which could break classical encryption schemes such as RSA and ECC. This ensures that Falcon remains a strong candidate for long-term cryptographic resilience. |
Low Overhead Cost
Falcon offers fast and lightweight signature verification, making it ideal for applications that need to process a high volume of transactions or messages quickly.
Compact Signature Size
Falcon has one of the smallest signature sizes among post-quantum algorithms, which is highly advantageous for applications where bandwidth, storage, or transmission size is limited (e.g., embedded systems, IoT devices).
Efficient Key Generation and signing
Falcon provides efficient key generation and signing processes, making it more suitable for environments with limited computational resources.
Lattice-Based Security
Falcon is based on lattice-based cryptography, which is widely regarded as one of the most secure cryptographic foundations in the post-quantum era. It provides strong security guarantees against both classical and quantum attacks.
NIST Standardization
Falcon has been selected as one of the finalists in the National Institute of Standards and Technology (NIST) post-quantum cryptography standardization process, lending it credibility and trust for future applications.
Post Quantum Security
Falcon is resistant to quantum attacks, particularly Shor’s algorithm, which could break classical encryption schemes such as RSA and ECC. This ensures that Falcon remains a strong candidate for long-term cryptographic resilience.
PQC Takes the Lead in Next-Gen Encryption Standards
Why are companies acting now?
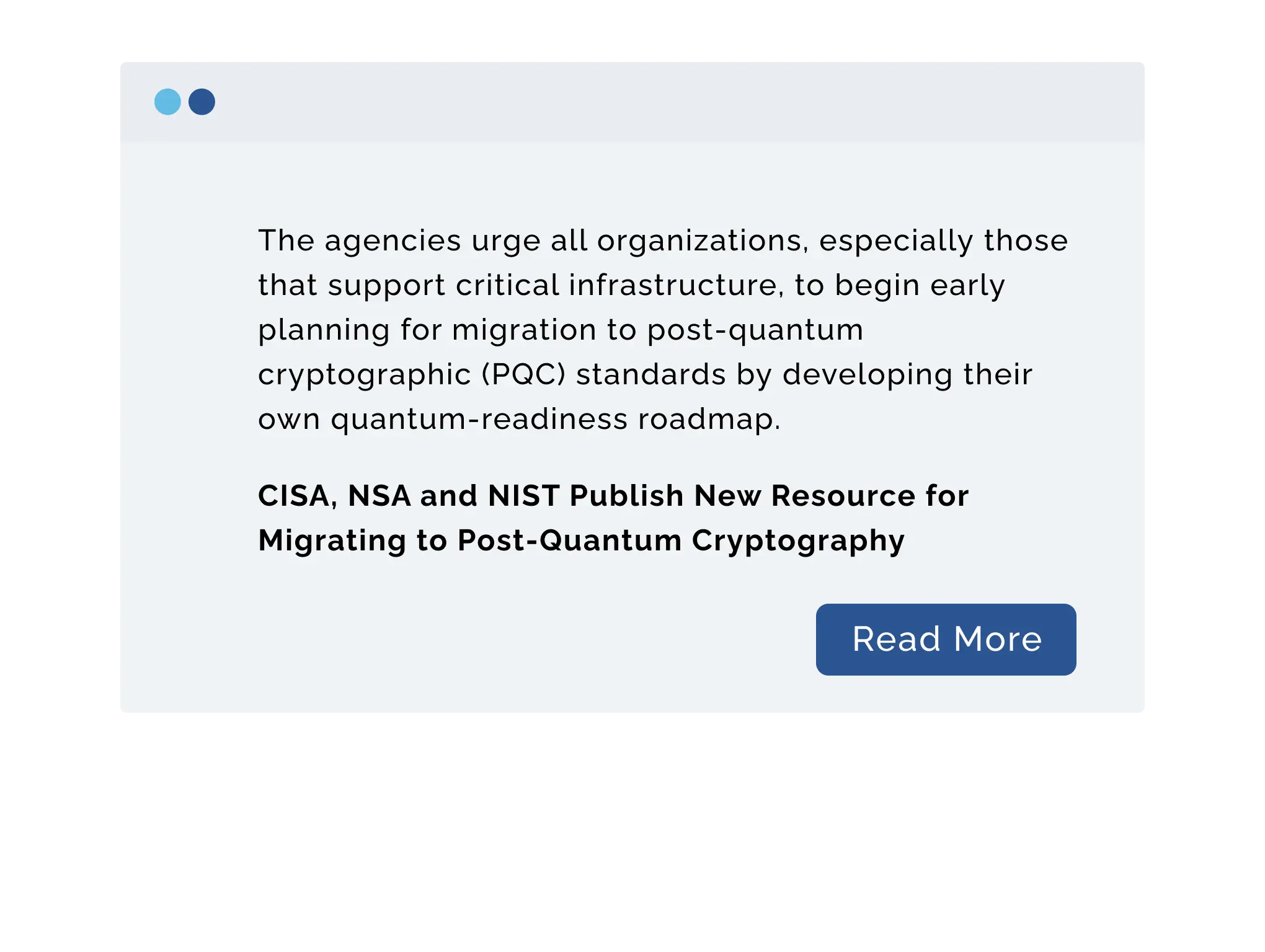
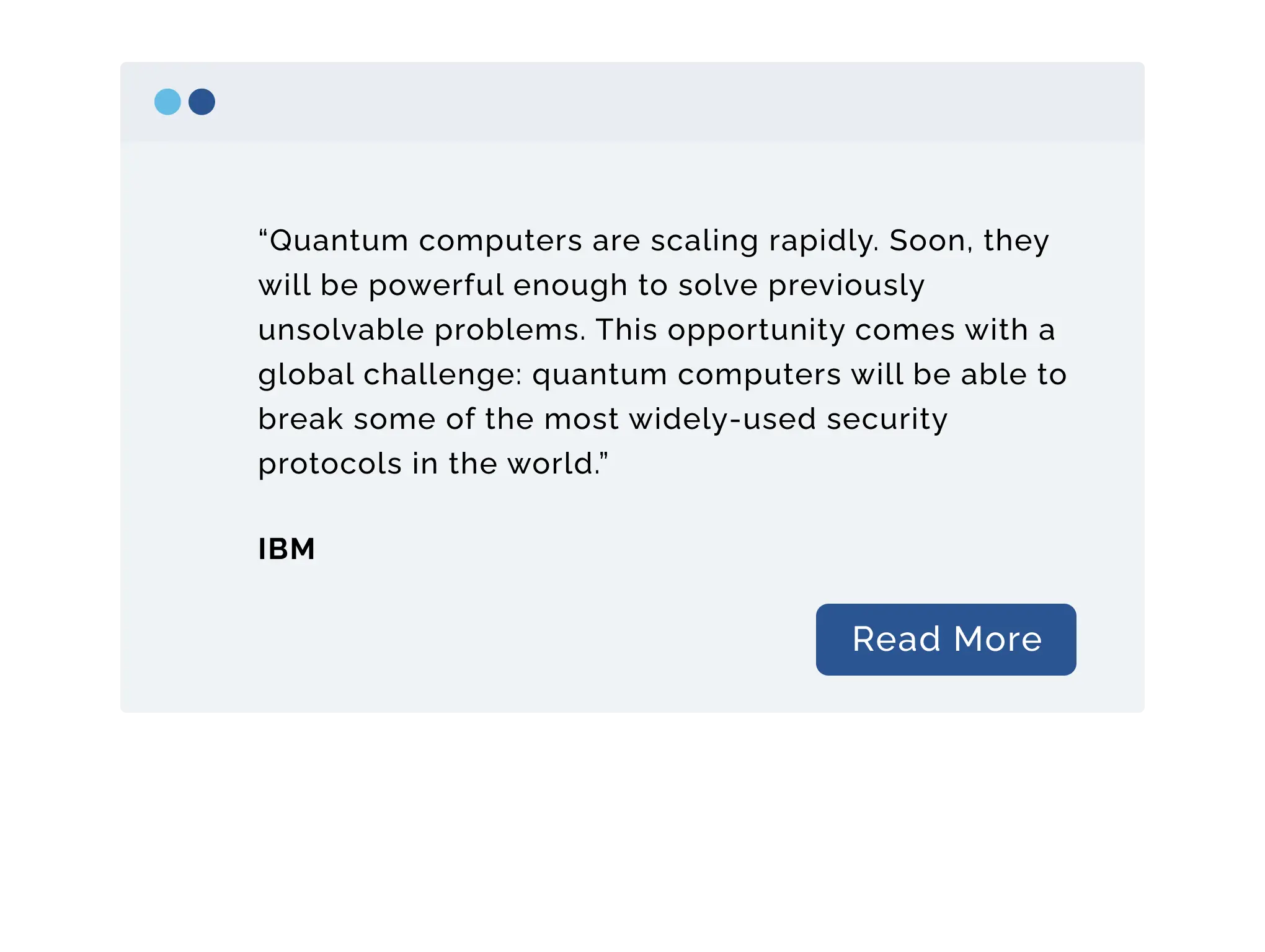
Why AES-256 Needs PQC for Future-Proof Security
While AES-256 remains a gold standard for encryption today, it is primarily designed to defend against classical computing attacks. As quantum computing advances, certain algorithms—especially those used for key exchange and digital signatures—could become vulnerable. To ensure long-term data security, AES-256 must be paired with post-quantum cryptography (PQC), which is specifically built to withstand the power of quantum attacks. This combination provides future-ready protection for sensitive data.
How PQC Benefits AES-256 Against Quantum Threats
| PQC Benefits To AES-256 | Description |
|---|---|
| Quantum Resistance for Asymmetric Cryptography | PQC encryption algorithms are specifically designed to be resistant to quantum computers. Quantum computers, using algorithms like Shor's, could break widely used asymmetric encryption methods such as RSA and ECC by efficiently factoring large numbers or solving discrete logarithms. |
| Asymmetric Encryption and Key Exchange Security | PQC algorithms provide quantum-safe solutions for asymmetric encryption, key exchange, and digital signatures, which are critical for secure communications (e.g., TLS, VPNs). They allow two parties to exchange keys over insecure channels in a quantum-safe manner, which is essential for long-term data protection. |
| Long-Term Data Protection | PQC encryption ensures that data encrypted today remains secure against future quantum computers. This is especially important for sensitive data that needs to remain protected for many years, such as in healthcare, government, or financial services. |
| Digital Signature and Authentication Security | PQC encryption offers quantum-safe digital signatures and authentication mechanisms. These are essential for ensuring the integrity and authenticity of messages or software updates, especially in systems like blockchain, secure communication protocols, or IoT devices. |
| Protection Against Future Threats | PQC algorithms offer protection against future quantum computers that could render many current encryption methods obsolete. As quantum computing technology advances, PQC encryption is necessary to future-proof secure communication and data storage. |
| Broader Cryptographic Functions | PQC algorithms support a broader range of cryptographic functions beyond data encryption, including key exchange, digital signatures, and identity verification, which are crucial for secure communication, blockchain technology, and digital identity management. |
Quantum Resistance for Asymmetric Cryptography
PQC encryption algorithms are specifically designed to be resistant to quantum computers. Quantum computers, using algorithms like Shor’s, could break widely used asymmetric encryption methods such as RSA and ECC by efficiently factoring large numbers or solving discrete logarithms.
Asymmetric Encryption and Key Exchange Security
PQC algorithms provide quantum-safe solutions for asymmetric encryption, key exchange, and digital signatures, which are critical for secure communications (e.g., TLS, VPNs). They allow two parties to exchange keys over insecure channels in a quantum-safe manner, which is essential for long-term data protection.
Long-Term Data Protection
PQC encryption ensures that data encrypted today remains secure against future quantum computers. This is especially important for sensitive data that needs to remain protected for many years, such as in healthcare, government, or financial services.
Digital Signature and Authentication Security
PQC encryption offers quantum-safe digital signatures and authentication mechanisms. These are essential for ensuring the integrity and authenticity of messages or software updates, especially in systems like blockchain, secure communication protocols, or IoT devices.
Protection Against Future Threats
PQC algorithms offer protection against future quantum computers that could render many current encryption methods obsolete. As quantum computing technology advances, PQC encryption is necessary to future-proof secure communication and data storage.
Broader Cryptographic Functions
PQC algorithms support a broader range of cryptographic functions beyond data encryption, including key exchange, digital signatures, and identity verification, which are crucial for secure communication, blockchain technology, and digital identity management.
Locktera Access Control Rules
Locktera’s Access Control Rules deliver powerful, customizable protection for your data. Rules are applied at the individual file level, allowing you to set unique permissions for each file based on user identity, location, IP address, and access rights. This granular approach ensures that only authorized individuals can interact with sensitive content. Combined with advanced encryption and detailed access logs, Locktera gives you complete visibility and control—enhancing security at every layer.
Have Questions About Locktera Security?
Locktera Access Controls
| Access Control | Description |
|---|---|
| Password Required | Require a viewer to enter a password up to 256 characters to access content files. Locktera does not store passwords. If the user forgets the password, containers cannot be accessed without it. |
| Lockout | Viewers have 5 attempts to successfully enter the correct password and access the container contents. On the 6th attempt, the viewer will be locked out and instructed to contact the sender. The locked container appears as locked on the sender's dashboard. To regain access, the sender must manually unlock the container, and the viewer can reattempt access via correct password entry. |
| Read Only Permission | The container contents can be designated for read-only access. Viewers cannot edit, download, print, or screen capture contents. |
| Download Permission | The viewer can download container contents. Content files downloaded to their local device by the viewer are no longer encrypted. Files that are incompatible with the browser will not render and must be shared, allowing the recipient to download the contents. This allows viewers to download the file to a local drive and access/view them via software located on the local device. Senders are instructed to choose "Allow Download" for files that are not viewable due to browser limitations. |
| Authorized Viewers | Designate people authorized to access content files. List authorized viewers by email, organization roles, groups, or allow anyone with the link to access. |
| Time-Limited Access | Specify a date range that authorized viewers must access container files. |
Password Required
Require a viewer to enter a password up to 256 characters to access content files. Locktera does not store passwords. If the user forgets the password, containers cannot be accessed without it.
Lockout
Viewers have 5 attempts to successfully enter the correct password and access the container contents. On the 6th attempt, the viewer will be locked out and instructed to contact the sender. The locked container appears as locked on the sender’s dashboard. To regain access, the sender must manually unlock the container, and the viewer can reattempt access via correct password entry.
Read Only Permission
The container contents can be designated for read-only access. Viewers cannot edit, download, print, or screen capture contents.
Download Permission
The viewer can download container contents. Content files downloaded to their local device by the viewer are no longer encrypted. Files that are incompatible with the browser will not render and must be shared, allowing the recipient to download the contents. This allows viewers to download the file to a local drive and access/view them via software located on the local device. Senders are instructed to choose “Allow Download” for files that are not viewable due to browser limitations.
Authorized Viewers
Designate people authorized to access content files. List authorized viewers by email, organization roles, groups, or allow anyone with the link to access.
Time-Limited Access
Specify a date range that authorized viewers must access container files.
Advanced Access Control Rules
| Advanced Control Rule | Description |
|---|---|
| Access Control |
Flexible Control: Allows container access rules to be modified. Content files are immutable, and the container password cannot be changed. Authorized viewers, download permission, location, IP address, and number of open rules can be modified. Fixed Control: Container fixed with the original access rules and authorized viewers. These containers cannot be modified. |
| Number of Sessions | Limit access to a specific number of Sessions. |
| Geographical Location | Locktera allows you to designate specific locations where containers can be accessed and block access from other locations. Multiple locations can be set for both access and restriction, using IP address geolocation to determine device locations. Geolocation is accurate to the city or region level. VPNs use their associated IP address geolocation for these rules. Designate the location where containers must be accessed. |
| IP Address | Locktera allows you to designate specific IP addresses for container access and block others, with the ability to set multiple addresses for both. IP rules can limit access to a company VPN or building Wi-Fi. Locktera uses Classless Inter-Domain Routing (CIDR) for efficient IP allocation. Blocked IP addresses are logged in an Access Denied Report for monitoring. Designate the IP address from which containers can be accessed. |
Access Control
Flexible Control: Allows container access rules to be modified. Content files are immutable, and the container password cannot be changed. Authorized viewers, download permission, location, IP address, and number of open rules can be modified.
Fixed Control: Container fixed with the original access rules and authorized viewers. These containers cannot be modified.
Number of Sessions
Limit access to a specific number of Sessions.
Geographical Location
Locktera allows you to designate specific locations where containers can be accessed and block access from other locations. Multiple locations can be set for both access and restriction, using IP address geolocation to determine device locations. Geolocation is accurate to the city or region level. VPNs use their associated IP address geolocation for these rules. Designate the location where containers must be accessed.
IP Address
Locktera allows you to designate specific IP addresses for container access and block others, with the ability to set multiple addresses for both. IP rules can limit access to a company VPN or building Wi-Fi. Locktera uses Classless Inter-Domain Routing (CIDR) for efficient IP allocation. Blocked IP addresses are logged in an Access Denied Report for monitoring. Designate the IP address from which containers can be accessed.
Key benefits of using Access Control rules for each secure container :
| Benefit | Description |
|---|---|
| Granular Security | Access can be tailored to individual users, locations, or IP addresses, ensuring that only authorized personnel have access to specific containers. |
| Enhanced Data Protection | By limiting who can view or modify data, you reduce the risk of unauthorized access, data breaches, or accidental changes. |
| Compliance Support | Access Control rules help enforce data security policies, making it easier to meet regulatory requirements like GDPR or HIPAA. |
| Audit and Monitoring | Access logs provide visibility into who accessed data and when, supporting security audits and enabling quick response to suspicious activity. |
| Flexibility | Multiple rules can be applied, allowing dynamic management of access across different users, departments, and geographic locations. |
| Reduced Attack Surface | By restricting access based on IP addresses, locations, or VPNs, you minimize potential entry points for attackers. |
Granular Security
Access can be tailored to individual users, locations, or IP addresses, ensuring that only authorized personnel have access to specific containers.
Enhanced Data Protection
By limiting who can view or modify data, you reduce the risk of unauthorized access, data breaches, or accidental changes.
Compliance Support
Access Control rules help enforce data security policies, making it easier to meet regulatory requirements like GDPR or HIPAA.
Audit and Monitoring
Access logs provide visibility into who accessed data and when, supporting security audits and enabling quick response to suspicious activity.
Flexibility
Multiple rules can be applied, allowing dynamic management of access across different users, departments, and geographic locations.
Reduced Attack Surface
By restricting access based on IP addresses, locations, or VPNs, you minimize potential entry points for attackers.
Optimized Data Transmission with TLS 1.3 Security.
Locktera enhances both security and performance during data transmission by leveraging TLS 1.3—the latest and most advanced transport layer encryption protocol. With reduced handshake latency, forward secrecy, and streamlined cipher suites, TLS 1.3 offers significant improvements over its predecessors. The table below highlights the key advantages of using TLS 1.3 in Locktera’s architecture.
Key Advantages of TLS 1.3
| Benefit | Description |
|---|---|
| Granular Security | Access can be tailored to individual users, locations, or IP addresses, ensuring that only authorized personnel have access to specific containers. |
| Enhanced Data Protection | By limiting who can view or modify data, you reduce the risk of unauthorized access, data breaches, or accidental changes. |
| Compliance Support | Access Control rules help enforce data security policies, making it easier to meet regulatory requirements like GDPR or HIPAA. |
| Audit and Monitoring | Access logs provide visibility into who accessed data and when, supporting security audits and enabling quick response to suspicious activity. |
| Flexibility | Multiple rules can be applied, allowing dynamic management of access across different users, departments, and geographic locations. |
| Reduced Attack Surface | By restricting access based on IP addresses, locations, or VPNs, you minimize potential entry points for attackers. |
Faster Handshake and Performance
TLS 1.3 reduces round-trip communications during the handshake process, enabling faster secure connections. The handshake requires only one round trip, reducing latency and improving user experience in high-traffic environments.
Stronger Encryption Algorithms
TLS 1.3 eliminates weaker cryptographic algorithms like RC4, SHA-1, and MD5, and mandates stronger ciphers like AES-256-GCM, ChaCha20-Poly1305, and ECDHE. These ensure resistance to cryptographic attacks.
Forward Secrecy By Default
TLS 1.3 enforces Forward Secrecy (FS) by default, ensuring that even if long-term keys are compromised, past communications remain secure. This protects sensitive data like encryption keys and confidential files.
Simplified Protocol, Reduced Attack Surface
TLS 1.3 removes outdated features like compression and renegotiation, reducing complexity and eliminating vulnerabilities from older versions. This makes Locktera less prone to attacks such as CRIME and BREACH.
Resistance to Downgrade Attacks
TLS 1.3 includes protections against downgrade attacks, ensuring connections use the strongest protocol version. This guarantees Locktera operates under the highest security standards during communications.
Improved Privacy
TLS 1.3 encrypts more handshake metadata, preventing eavesdroppers from accessing sensitive session information. This ensures confidentiality of session identifiers and encryption parameters.
Enhanced Security for Post-Quantum Readiness
TLS 1.3 supports advanced cipher suites and key exchange mechanisms, making it adaptable for quantum-resistant algorithms to secure future communications.
Have a Question? We’re Here to Help.
Deployment Options
LOCKTERA SHARE
CLOUD
Get immediate access via Locktera’s SAAS to get immediate access to your new full-featured secure file vault.
LOCKTERA SHARE
BRING YOUR OWN STORAGE
Use your own storage to maintain full custody of all of your data while Locktera’s SAAS runs the backend for you.
LOCKTERA SHARE
ON-PREM
Install a full deployment of Locktera within your own cloud tenant or on-premise environment if you require full control.
