Webinar:
EHR Implementation Success:
How To Avoid Blind Spots That Cost Millions
Webinar:
April 17th, 2025
11:00 am CST
EHR implementation doesn’t have to hurt. Yet, for many healthcare organizations, it does—budget overruns, missed deadlines, frustrated staff, and regulatory headaches, and all of this increases cost. Why? Because the root of the problem often goes unaddressed. Join Bear MCG and Locktera for a must-attend webinar for anyone involved in an EHR implementation.
You’ll walk away with:
✅ A deeper understanding of the hidden PM and CM pitfalls that cause cost overruns and sabotage EHR success
✅ Best practices to manage organizational change across your healthcare team
✅ Strategies for protecting sensitive health data during complex implementations
✅ A playbook for successful, secure EHR rollouts

View The Webinar Now!
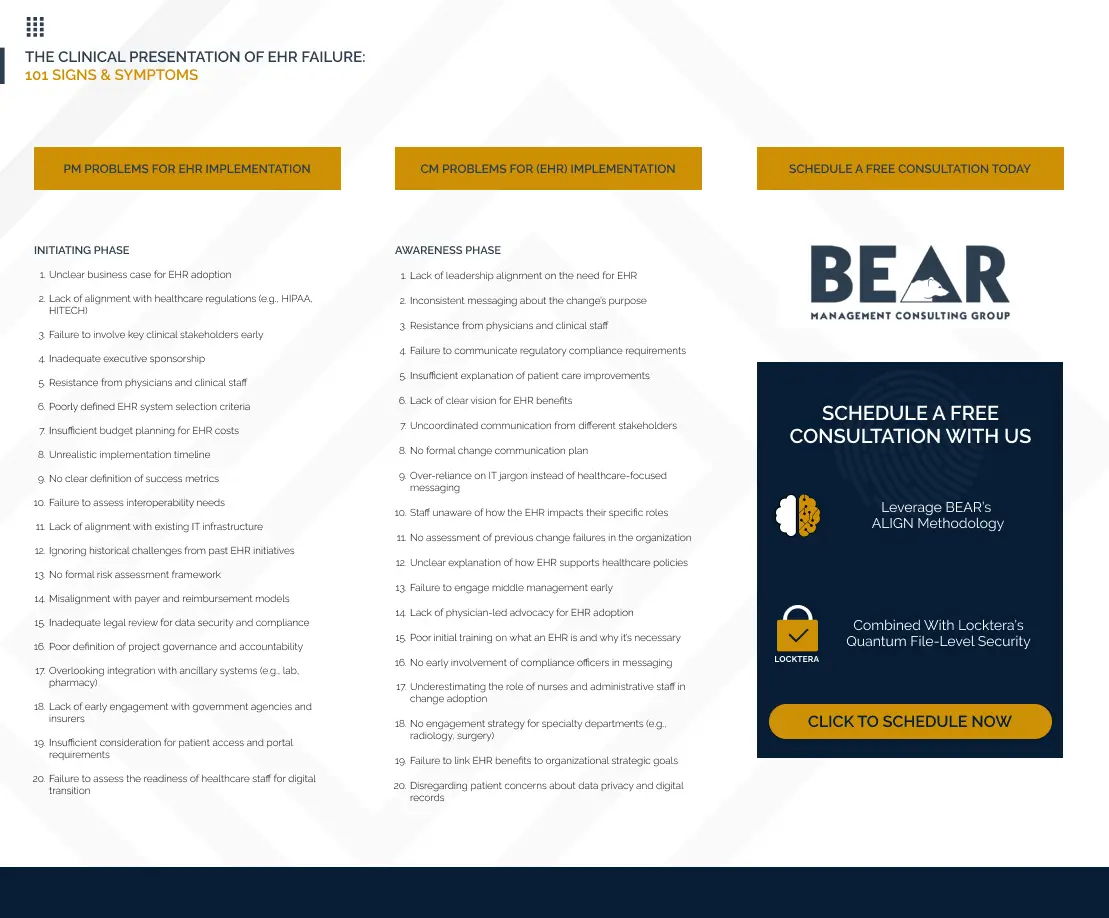
The Clinical Presentation of EHR Failure: 101 Signs & Symptoms
Download: 101 Signs & Symptoms of EHR Implementation Failure
EHR implementations can go off track—fast. Whether you’re a healthcare provider, consultant, or IT leader, understanding the early warning signs of failure is critical to course-correct and protect your investment.
“The Clinical Presentation of EHR Failure: 101 Signs & Symptoms” is a practical leave-behind guide designed to help teams recognize and respond to red flags before they escalate. Based on real-world implementations, this resource offers insight into what goes wrong—and how to fix it.
📥 Download now to get ahead of the problems and keep your EHR projects on the path to success.
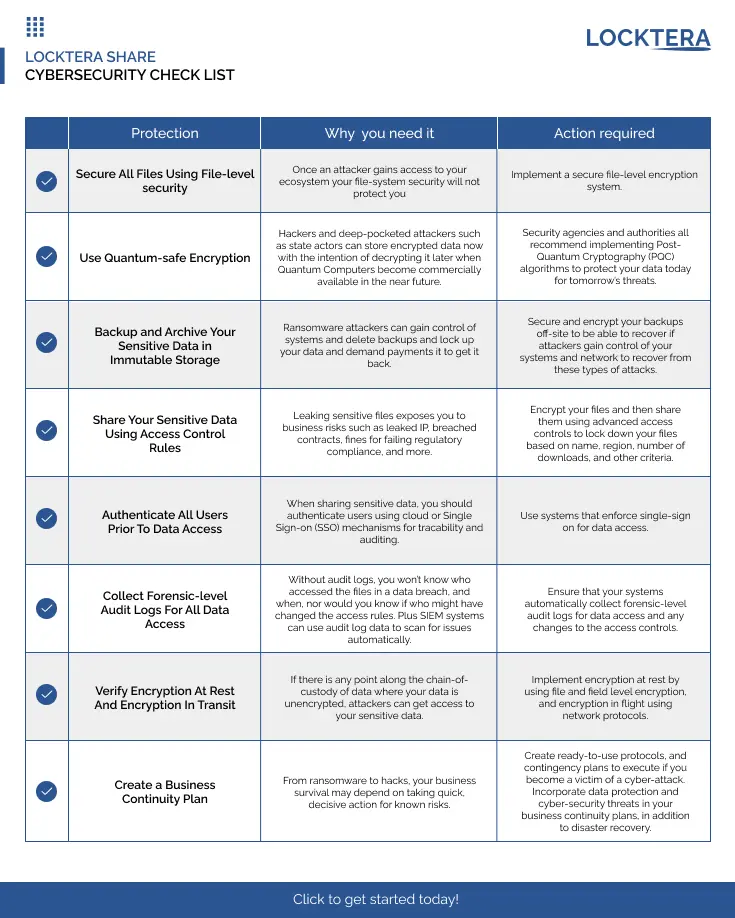
Locktera: Cybersecurity Checklist
Download: Cybersecurity Checklist for File-Level Protection
Cyber threats are evolving fast—and so should your defense. This Cybersecurity Checklist gives you a clear, actionable roadmap for protecting your organization’s most sensitive data from modern threats like ransomware, insider risk, and quantum-era decryption.
Built around best practices recommended by top security authorities, this checklist walks you through the essentials—from file-level encryption and access controls, to immutable backups, forensic audit trails, and business continuity planning.
Download now to assess your current posture and implement the protections that matter most—before an attacker forces the issue.